CentOS7.9搭建L2TP
Sonder
9天前
6893字
17分钟
浏览 (134)
CENTOS7搭建L2TP OVER IPSEC
当前系统:
# 镜像源: CentOS 7.9 64位
CentOS Linux release 7.9.2009 (Core)一、这是检测服务器支不支持搭建的方法
先看看你的主机是否支持pptp,返回结果为yes就表示通过。
modprobe ppp-compress-18 && echo yes是否开启了TUN,有的虚拟机主机需要开启,返回结果为cat: /dev/net/tun: File descriptor in bad state,或者cat: /dev/net/tun: 文件描述符处于错误状态就表示通过。
cat /dev/net/tun二、正式搭建命令
- 首先一台全新的服务器记得换源
- 安装必要程序
- 编辑pppoptfile文件
- 修改L2tp的配置文件
- 添加账号密码
- 创建预共享密钥
- 修改内核参数
- 建立ipsec 与 l2tp 服务关联的配置文件
- iptables安装配置
- 启动
1.首先一台全新的服务器记得换源
yum install -y epel-release2.安装这一堆花里胡哨的必要程序
yum install -y make gcc gmp-devel xmlto bison flex xmlto libpcap-devel lsof vim-enhanced man xl2tpd libreswan nano3.编辑 pppoptfile 文件
# mv /etc/ppp/options.xl2tpd /etc/ppp/options.xl2tpd.old
vim /etc/ppp/options.xl2tpdrequire-mschap-v2
ipcp-accept-local
ipcp-accept-remote
ms-dns 8.8.8.8
ms-dns 1.1.1.1
# ms-dns 192.168.1.1
# ms-dns 192.168.1.3
# ms-wins 192.168.1.2
# ms-wins 192.168.1.4
noccp
auth
#obsolete: crtscts
idle 1800
mtu 1410
mru 1410
nodefaultroute
debug
#obsolete: lock
proxyarp
connect-delay 5000
# To allow authentication against a Windows domain EXAMPLE, and require the
# user to be in a group "VPN Users". Requires the samba-winbind package
# require-mschap-v2
# plugin winbind.so
# ntlm_auth-helper '/usr/bin/ntlm_auth --helper-protocol=ntlm-server-1 --require-membership-of="EXAMPLE\\VPN Users"'
# You need to join the domain on the server, for example using samba:
# http://rootmanager.com/ubuntu-ipsec-l2tp-windows-domain-auth/setting-up-openswan-xl2tpd-with-native-windows-clients-lucid.html4.修改L2tp的配置文件
# mv /etc/xl2tpd/xl2tpd.conf /etc/xl2tpd/xl2tpd.conf.old
vim /etc/xl2tpd/xl2tpd.conf;
; This is a minimal sample xl2tpd configuration file for use
; with L2TP over IPsec.
;
; The idea is to provide an L2TP daemon to which remote Windows L2TP/IPsec
; clients connect. In this example, the internal (protected) network
; is 192.168.1.0/24. A special IP range within this network is reserved
; for the remote clients: 192.168.1.128/25
; (i.e. 192.168.1.128 ... 192.168.1.254)
;
; The listen-addr parameter can be used if you want to bind the L2TP daemon
; to a specific IP address instead of to all interfaces. For instance,
; you could bind it to the interface of the internal LAN (e.g. 192.168.1.98
; in the example below). Yet another IP address (local ip, e.g. 192.168.1.99)
; will be used by xl2tpd as its address on pppX interfaces.
[global]
listen-addr = 114.55.91.105 #改成自己的外网IP
;
; requires openswan-2.5.18 or higher - Also does not yet work in combination
; with kernel mode l2tp as present in linux 2.6.23+
ipsec saref = yes
; Use refinfo of 22 if using an SAref kernel patch based on openswan 2.6.35 or
; when using any of the SAref kernel patches for kernels up to 2.6.35.
; saref refinfo = 30
;force userspace = yes
; force userspace = yes
;
; debug tunnel = yes
[lns default]
ip range = 192.168.1.100-192.168.1.254
local ip = 192.168.1.99
require chap = yes
refuse pap = yes
require authentication = yes
name = LinuxVPNserver
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes记得修改listen-addr里面的IP,改成自己的公网IP,我的公网IP是:114.55.91.105
5.添加账号密码
# mv /etc/ppp/chap-secrets /etc/ppp/chap-secrets.old
vim /etc/ppp/chap-secrets# Secrets for authentication using CHAP
# client server secret IP addresses
test * abc456 *6.创建预共享密钥
vim /etc/ipsec.d/ipsec.secrets#include /etc/ipsec.d/*.secrets
114.55.91.105 %any: PSK "abc456"记得修改里面的IP,改成自己的公网IP
7.修改内核参数
# mv /etc/sysctl.conf /etc/sysctl.conf.old
vim /etc/sysctl.conf# sysctl settings are defined through files in
# /usr/lib/sysctl.d/, /run/sysctl.d/, and /etc/sysctl.d/.
#
# Vendors settings live in /usr/lib/sysctl.d/.
# To override a whole file, create a new file with the same in
# /etc/sysctl.d/ and put new settings there. To override
# only specific settings, add a file with a lexically later
# name in /etc/sysctl.d/ and put new settings there.
#
# For more information, see sysctl.conf(5) and sysctl.d(5).
vm.swappiness=0
net.core.somaxconn=1024
net.ipv4.tcp_max_tw_buckets=5000
net.ipv4.tcp_max_syn_backlog=1024
net.ipv4.ip_forward = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.eth0.accept_redirects = 0 #每三句对应一个网卡
net.ipv4.conf.eth0.rp_filter = 0
net.ipv4.conf.eth0.send_redirects = 0
net.ipv4.conf.lo.accept_redirects = 0
net.ipv4.conf.lo.rp_filter = 0
net.ipv4.conf.lo.send_redirects = 0使配置生效
sysctl -p8.建立ipsec 与 l2tp 服务关联的配置文件
vim /etc/ipsec.d/l2tp_psk.confconn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
dpddelay=30
dpdtimeout=120
dpdaction=clear
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=114.55.91.105
leftprotoport=17/1701
right=%any
rightprotoport=17/%any记得修改里面left=114.55.91.105的IP,改成自己的公网IP
9.iptables安装配置
是用来管理防火墙的命令工具
yum install -y iptables
yum install -y iptables-servicessystemctl stop firewalld
systemctl mask firewalldiptables -L -niptables -P INPUT ACCEPT
iptables -F
iptables -X
iptables -Ziptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth0 -j MASQUERADE
iptables -I FORWARD -s 192.168.1.0/24 -j ACCEPT
iptables -I FORWARD -d 192.168.1.0/24 -j ACCEPT
iptables -A INPUT -p udp -m policy --dir in --pol ipsec -m udp --dport 1701 -j ACCEPT
iptables -A INPUT -p udp -m udp --dport 1701 -j ACCEPT
iptables -A INPUT -p udp -m udp --dport 500 -j ACCEPT
iptables -A INPUT -p udp -m udp --dport 4500 -j ACCEPT
iptables -A INPUT -p esp -j ACCEPT
iptables -A INPUT -m policy --dir in --pol ipsec -j ACCEPT
iptables -A FORWARD -i ppp+ -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
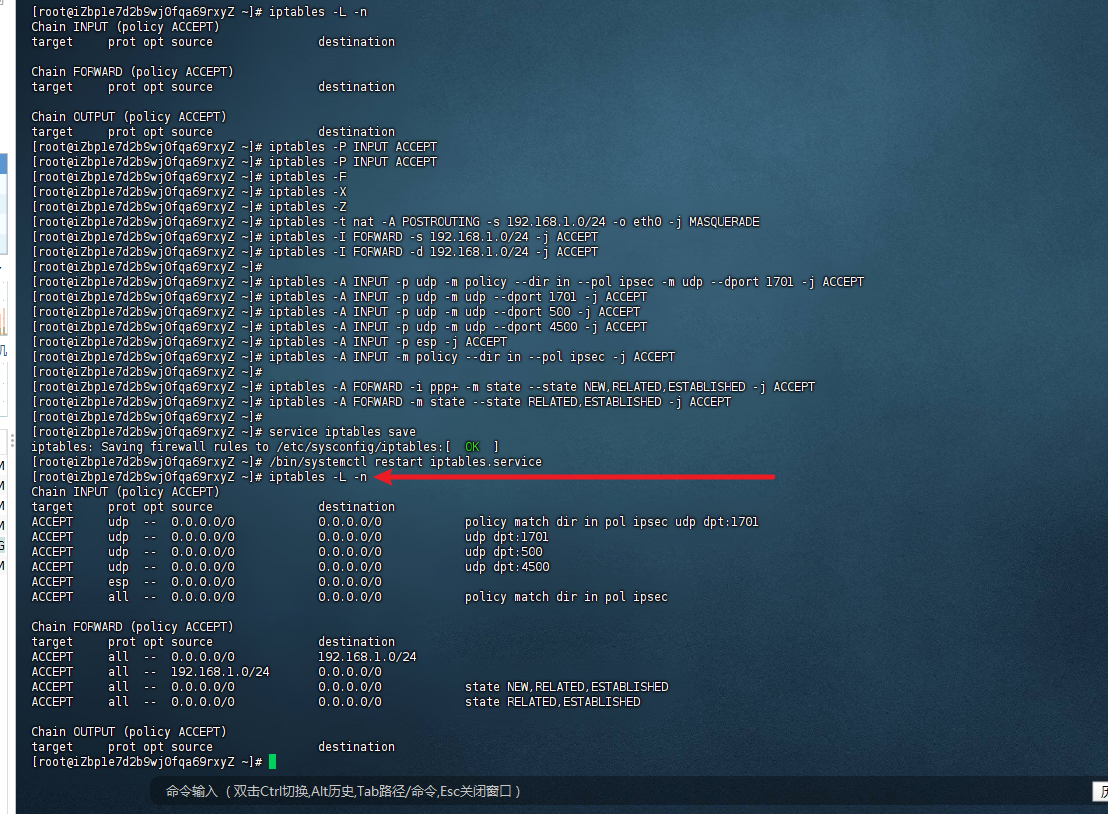
service iptables save
/bin/systemctl restart iptables.service然后再执行iptables -L -n进行查看
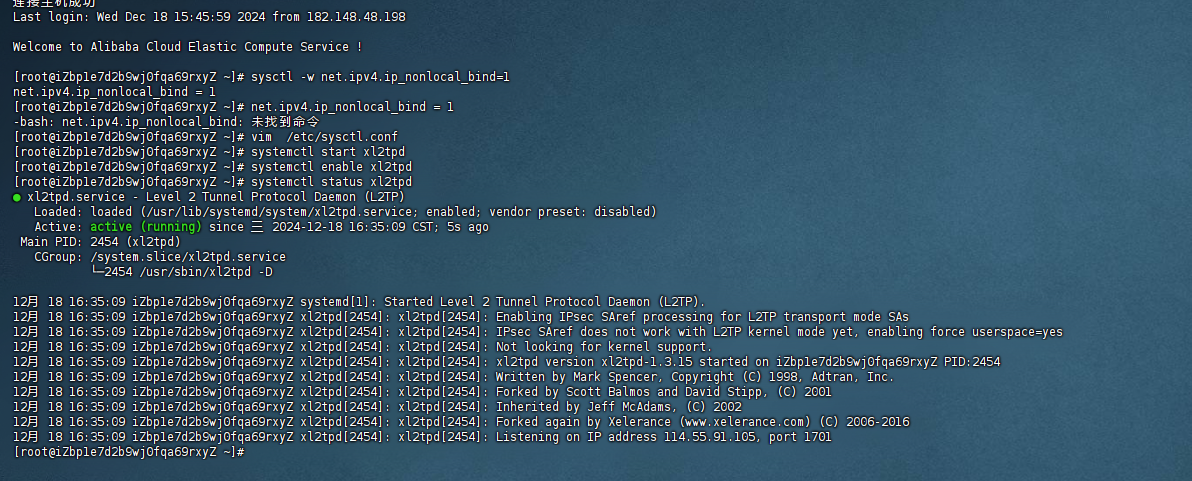
10.启动,分开执行,看看有没有错
systemctl start ipsecsystemctl enable ipsecipsec verifysystemctl start xl2tpdsystemctl enable xl2tpdsystemctl status xl2tpd使用预共享密钥的L2TP/IPsec
服务器地址:
预共享密钥:abc456
账号一:test
密码:abc456成功启动
常见问题
1.status 无法启动
systemctl status xl2tpd 无法启动
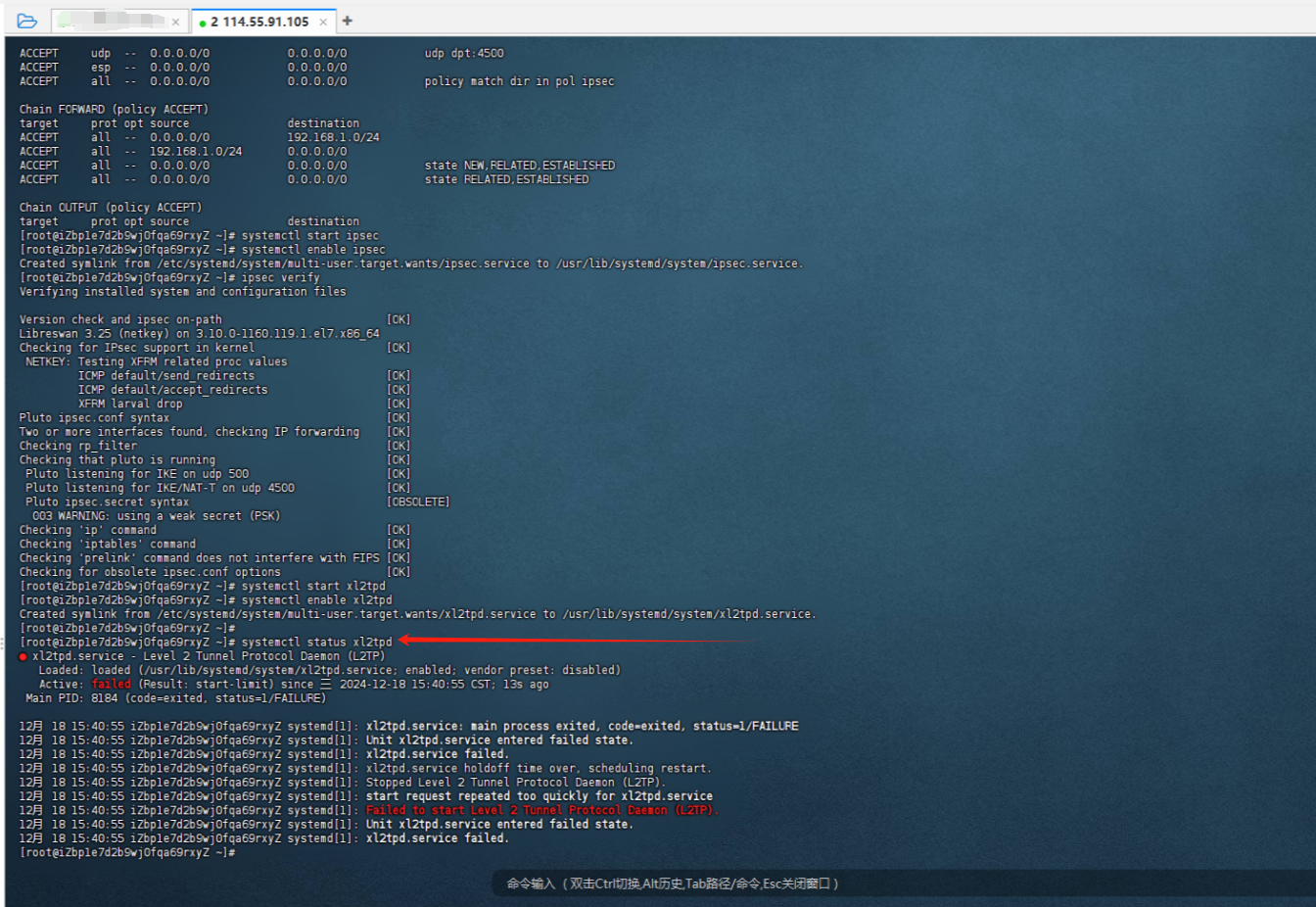
解决方法:
参考网址:xl2tpd 无法启动
使用 VRRP 提供故障转移,并且 VPN 外部地址配置有 VRRP 虚拟地址。
当路由器不是 VRRP 主路由器(这里就是这种情况)时,L2TP 无法绑定到非本地 IP 并且无法启动。
这是 Linux 默认配置,可以通过以下命令覆盖:
sysctl -w net.ipv4.ip_nonlocal_bind=1为了使其在重启后继续生效,我们需要在vim /etc/sysctl.conf 中添加以下行
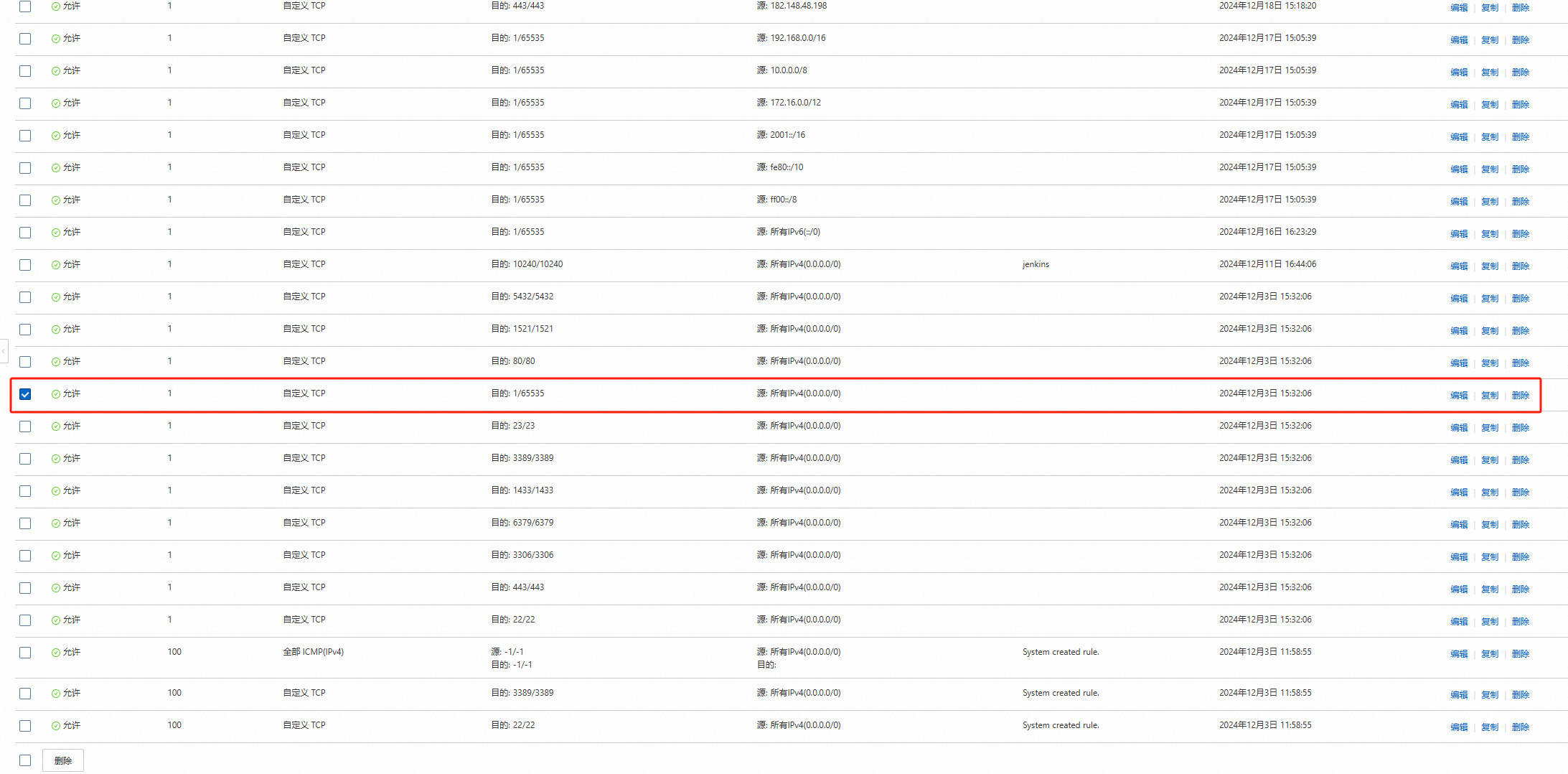
net.ipv4.ip_nonlocal_bind = 12.阿里云安全组
因为是试用服务器,我把自定义 UDP和自定义 TCP的入方向所有端口都开启了
参考博文
- 按照个博文进行搭建的,并进行修改:CENTOS7搭建L2TP OVER IPSEC
- 这篇博文常见问题都能解决:CentOS 7搭建L2TP VPN
